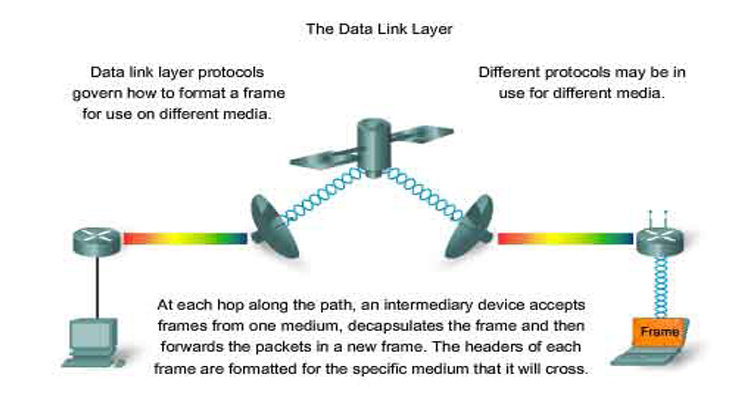
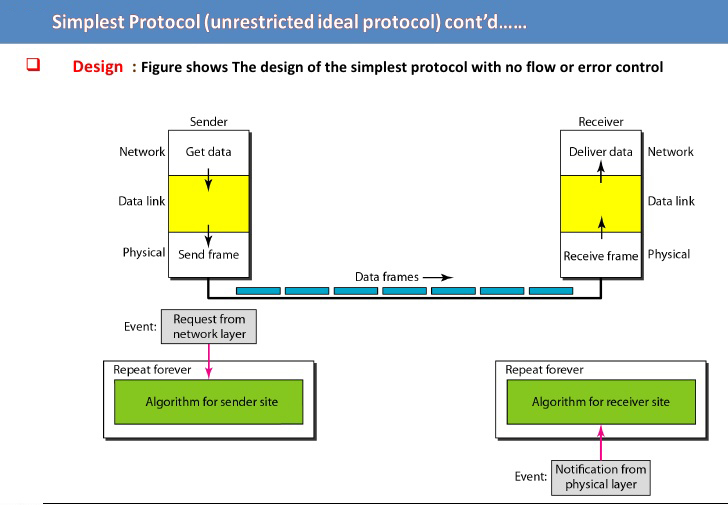
A network contains a large number of computers and various intermediate devices. All these devices and computers must be joined so as to transfer data from one computer of network to any other computer. This can be possible by using two methods:-
The first method is to create an individual wire link from every computer to every other computer (like fully connected topology) this method requires a lot of wiring and will increase the system cost and efficiency. The other method is to use a technique of switching. In a switched network, special devices called switches, are used to join two or more computers and intermediate devices with each other. Switches can create temporary connection between two devices attached to the switch. These devices are hardware devices that may have a software component in them. When a particular virtual path is to be set, the switch is set accordingly, to create a path between two nodes.
Read more